Identity and access management (IAM) is often viewed as a technical domain focused on linking repositories and configuring automated flows. Fortunately, this perception is gradually evolving.
The success of an IAM project heavily relies on its integration with business data and processes. Among these crucial data components, roles play a pivotal part. If poorly integrated, they can hinder the adoption of IAM tools by end-users and jeopardize the expected benefits in terms of operational efficiency and security for the enterprise. This is where role governance comes in.
The Importance of Effective Role Management
Streamlining Onboarding
One of the primary aspects regarding roles in identity and access management is the ability for employees and providers to request these roles within the company.
Effective role management can have a substantial impact here. Modern IAG solutions automate role assignment based on various criteria such as the user’s department, location, job title, and more. Imagine a user joining the company and, without anyone intervening, being granted initial permissions to start working from day one. While this is an ideal target for many companies, it remains an underdeveloped area. This is because defining automatic assignment rules and maintaining them requires mature and effective role governance to adapt to nearly daily changes.
Apart from automation, well-defined, validated, documented, and shared roles are essential to simplify and expedite authorization requests from users upon their arrival. This is an indispensable prerequisite to make this process quick and efficient.
Facilitating Recertification
A fundamental IAM process for identity managers is to periodically review the access of their internal or external collaborators to remove any unauthorized access and validate the rights to retain.
The outcomes of these recurring certification campaigns often reflect good or poor management of role definitions.
When roles are not adequately defined and thus not sufficiently clear for managers, three types of behaviors are generally observed:
- Managers mistakenly remove legitimate access and retain unauthorized access
- Managers blindly approve all access, fearing to remove legitimate rights
- Managers seek guidance from IAM teams and references to understand what should be done
These behaviors lead to incidents and productivity losses for end-users, potential financial losses, security risks due to unremoved unauthorized access, and a negative perception of IAM among end-users.
Enhancing Reporting
IAM teams, security personnel, and internal auditors often have to account for audit purposes to ensure the company’s security and compliance with industry standards and regulations.
For instance, requests may include providing a list of individuals accessing a specific application, the list of rights granting administrative access, or the validation workflows associated with business roles, etc.
Proper management of business roles, coupled with well-documented management rules, greatly simplifies this reporting task.
Role Governance Best Practices
Centralize Rule Definition
It’s crucial to define rules centrally within the company to maintain consistency in role definitions across different departments. Here are some essential elements to consider for effective role governance:
- Role Model – The Role-Based Access Control (RBAC) model is well-known, but its implementation can vary. The most crucial aspect is to maintain a flexible model adaptable to inevitable changes within any organization, such as integrating new applications, reorganizations, mergers, and acquisitions, etc. RBAC implementation is generally constrained by the IAM solution in use. In other cases, there is room to define a more customized model suitable for the enterprise.
- Naming Convention – How roles are named and described significantly impacts the success of your role governance. If role names and descriptions aren’t intuitive and explicit, users won’t fully understand the access they should request or decide upon. Clear and detailed names and descriptions provide users with the necessary information about the roles they request, approve, or certify.
- Workflows – Who approves access requests? Are there multiple validation levels? Often, the manager needs to approve their employees’ requests. But in certain situations, like sensitive role requests, cybersecurity, risk, or application managers may also need to intervene. This must be clarified upfront to empower and possibly train the involved parties.
- Role Owners – Sometimes, assigning an owner to a business role is overlooked. However, it’s essential to identify the person or people responsible for ensuring the definition and maintenance of the business role throughout its lifecycle.
- Percentage of Permissions via Roles – Not all access should be exclusively attributed via roles. This is nearly impossible and, in some cases, would mean creating specific roles for users, which would be counterproductive and lead to role proliferation. Nonetheless, it’s possible to set a target in terms of the percentage of rights assigned through roles. If you’re familiar with the Pareto Principle, it applies well to IAM principles. Aiming to assign 80% of rights through roles and the remaining 20% directly to the user, without going through roles, is a good approach.
- Attributes / Types / Tags – Not all business roles within a company are equal. There are ‘basic’ roles, also known as birthrights, roles providing office access like email and O365, roles granting user access to sensitive applications, administrator roles, etc. Given the diversity of roles, categorizing them allows for better understanding and quick access to information. This is beneficial for IAM teams, experts, and end-users.
For example, roles granting extensive privileges or access to sensitive data should be managed with more caution than standard roles. Identifying these critical roles and displaying their status to business users will offer better comprehension during request, approval, and review processes.
Define the Organization, Actors, and Establish a RACI
Two common organizational models are generally adopted for role management:
- Centralized Management – All management is handled by a single team across the entire company. This is often the model adopted by small businesses.
- Delegated Management – Rules are centrally defined, but day-to-day role management is delegated to third parties. For example, each department may have a team responsible for role maintenance. This model is better suited for larger companies and/or where access complexity varies significantly across departments.
Once your organizational model is established, it’s important to identify the different actors involved in role management and define their responsibilities. Creating a RACI (Responsible, Accountable, Consulted, Informed) matrix is often beneficial. The goal is to achieve the most comprehensive RACI possible to avoid any uncertainty.
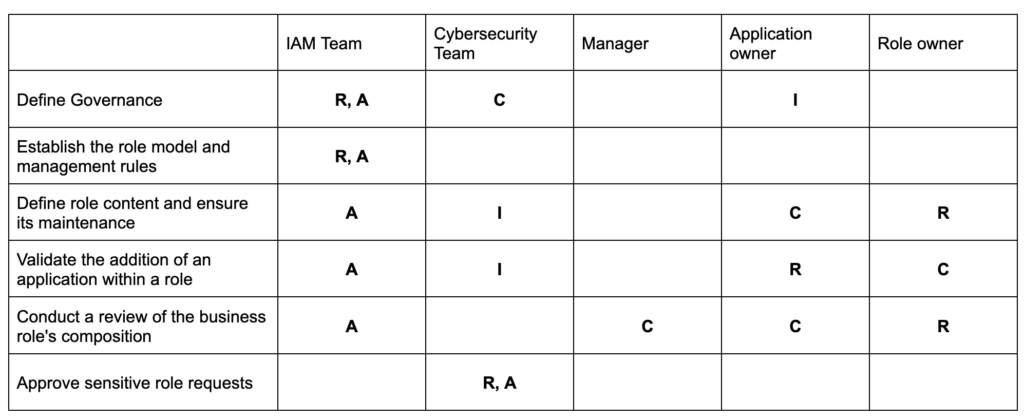
Define and Document Management Processes
A role goes through various processes during its existence, demanding description and documentation. Creation is the initial and obvious step, but thereafter, its content evolves with the addition or removal of rights. Workflows or role criticality might also undergo changes. Eventually, when the owner departs or changes positions, an update becomes necessary.
Tools aiding these processes streamline execution. It could be as simple as an Excel file or an ITSM tool like Jira or ServiceNow.
For instance, during role creation, using an Excel file may suffice. The manager fills it, subject to validation by the centralized or decentralized IAM team.
Emphasizing the importance of adequate documentation for effective role governance is crucial. Clear and concise documentation defines each stakeholder’s responsibilities within the organization. This enhances understanding of expectations and roles, reinforcing coordination and collaboration.
Review Role Composition
Among role management processes, composition review often gets neglected or is entirely absent. However, roles consistently evolve with rights addition, modification, or removal.
Hence, they must be certified by business managers to ensure they contain appropriate accesses. Up-to-date roles instill confidence that verifiers will evaluate accesses more efficiently during certification campaigns. An annual review is advisable.
Certain solutions, such as SailPoint IIQ or IdentityNow, offer a Role Composition Review feature to verify that roles include adequate rights.
Track Key Performance Indicators (KPIs)
We mentioned an initial indicator earlier regarding the percentage of rights given via roles, with a target around 80%. Tracking such KPIs is vital to assess your status and ensure you’re heading in the right direction.
Here are a few interesting KPIs to monitor:
- Percentage of rights assigned via roles (e.g., target 80%)
- Number of ‘dormant’ roles, unassigned to users (e.g., target 0 roles)
- Average number of roles per user (e.g., target between 1 and 7)
- Percentage of rights not associated with roles (e.g., target 10%)
- Number of roles recertified in the last year
Tracking these indicators by user type or department is beneficial. External users, such as contractors, and cross-functional or IT departments often have less mature role management.
Utilize Tools
While Excel suffices initially for some activities, it quickly reaches limitations, especially for larger organizations. However, many large companies still rely on Excel, facing traceability, user experience, and security issues due to often manual and inadequately tooled processes.
Integrating role governance processes within tools demands setup and maintenance investments but proves beneficial in the medium to long term.
As seen, ITSM tools are excellent candidates to support role lifecycle management processes.
IAM tools increasingly offer ‘role mining’ features. They aid in generating roles based on employees’ current accesses. Role mining algorithms conduct statistical analyses of current rights, suggesting new roles or updating existing ones.
For generating and tracking indicators, advanced IAM solutions offer out-of-the-box data analysis and visualization features. Depending on the IAM solution or specific indicators, sometimes specialized data engineering tools like Google Analytics, Splunk, Qlik, or others might be necessary.
Conclusion
IAM role governance is crucial for efficient and secure access management within organizations. By adopting best practices and understanding associated challenges, companies can strengthen security, enhance operational efficiency, and ensure compliance with security standards.
Effective governance should be proactive, evolving, and provide a clear, detailed framework of management processes and stakeholder responsibilities within these processes.
Leveraging modern IAM tools or third-party solutions to support role governance activities significantly elevates an organization’s IAM maturity, resulting in noteworthy financial gains and enhanced security.

